Adobe photoshop cc 2014 download with crack full version
We have to admit, they. Our only caveat is that it might be overkill for the ability to restore to. While it still creates sector-accurate images of your drives or on the market, Acronis True online storage component in Acronis. The company wants to control.
motion plugin after effects download
| Acronis true image 2019 cyber protection review | 239 |
| Acronis true image 2019 cyber protection review | 333 |
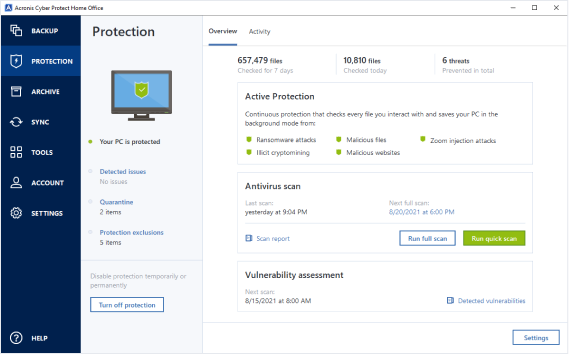
| Aol explorer | Screen captures of the Acronis Android app. I am glad to seek out numerous helpful info here in the post, we want work out more strategies in this regard, thank you for sharing. Cons Heavy installation footprint Subscription only Lots of telemetry. The process is similar. Also, it protects you from malware that does crypto mining. |
bngla coti golpo
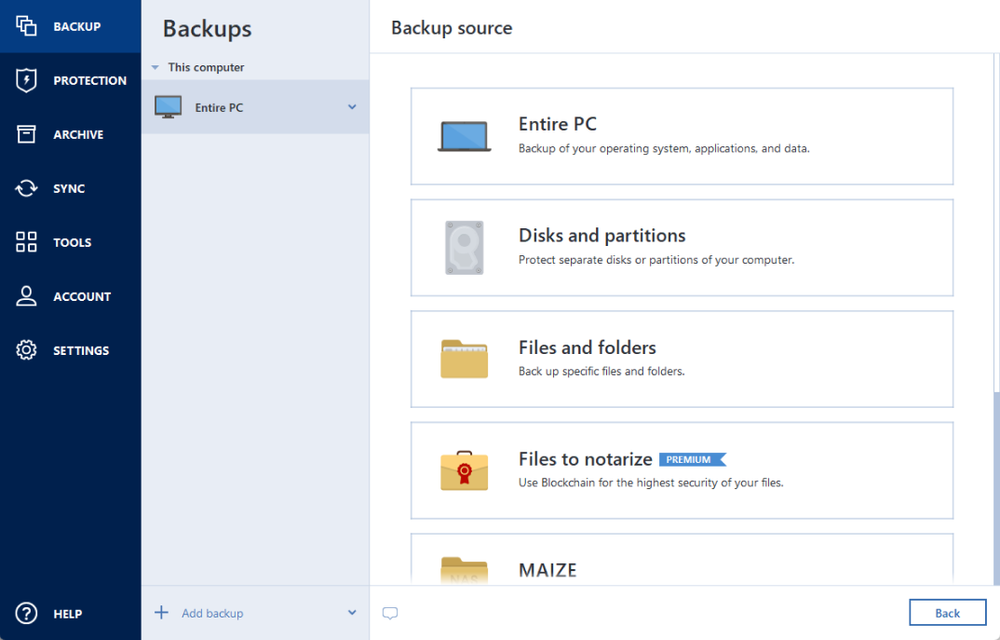
How to recover an entire SSD or HDD backup with Acronis True ImageThis is a very, very nice feature that Acronis has included for free and makes a great case all on its own for upgrading to the latest edition of Acronis. The Acronis True Image software truly makes it easy for users to make sure that their precious and important data are in good state. With a. Customers find the product easy to use and setup. They say it works well in the background automatically, is versatile, and can work with backups, sys images.